Security
Okta SSO
Setting up Okta to work with Chalk
Chalk is capable of using standard SSO providers like Google and GitHub for SSO authentication. For companies that use Okta, additional configuration is required.
Supported Features
- IDP-initiated Single Sign-On (OpenID Connect), initiated via Okta
- SP-initiated Single Sign-On (OpenID Connect), initiated from Chalk
Requirements
- Configure a custom OIDC app in Okta’s dashboard
- Send configuration parameters to Chalk support
Configuration Steps
Currently, Chalk requires a custom OIDC app integration to work with Okta for SSO.
- Navigate to your admin dashboard (
https://<your-domain>.okta.com/admin/apps/active) - Choose “Create App Integration”
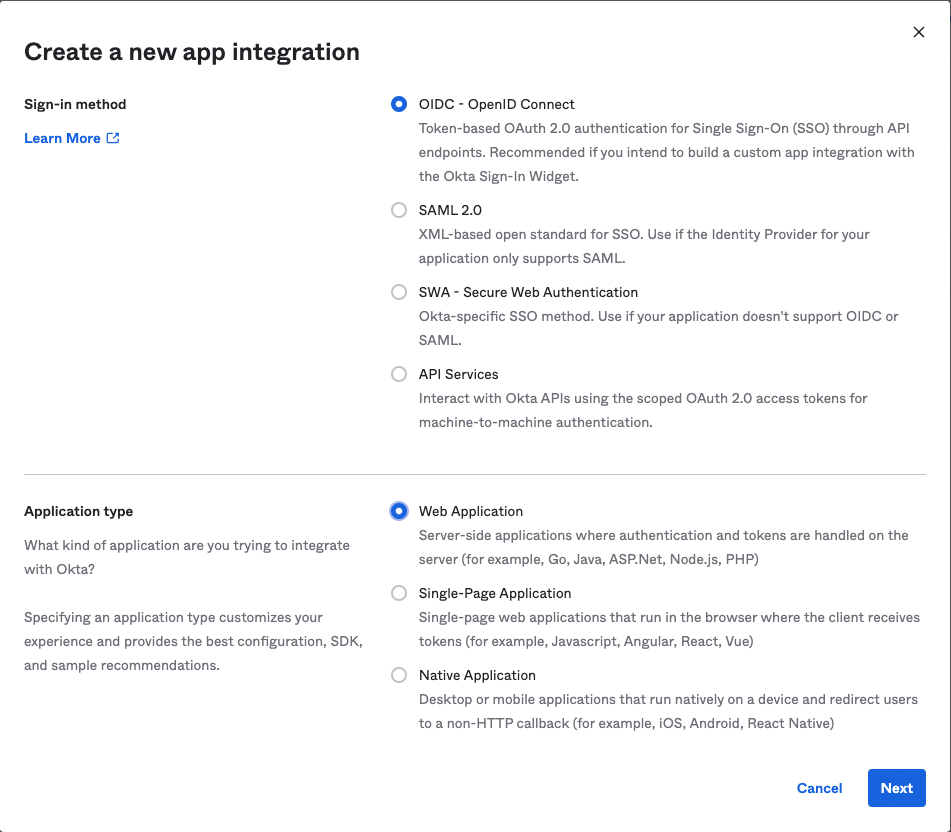
- Choose “OIDC - OpenID Connect” for “Sign-in Method”
- Choose “Web Application” for “Application type”
- Configure the Web App Integration
- App integration name:
Chalk - Logo: Chalk logo is available here
- Grant type: Ensure that
Authorization Codeis checked - Sign-in redirect URIs:
https://chalk.ai/api/auth/callback/okta - Sign-out redirect URIs
https://chalk.ai/api/oidc/post-logout
- App integration name:
- After clicking “save”, copy the “Client ID” and a “Client Secret” from the Client Credentials section on the application configuration page
- Submit the “Client ID” and “Client Secret” to Chalk Support, along with your Okta domain (your “issuer”)